[ad_1]


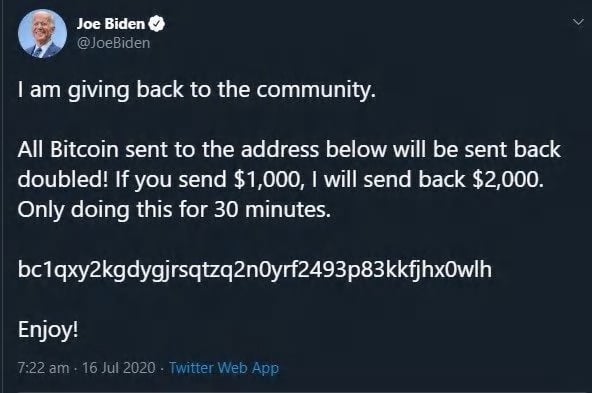
On Wednesday, a large number of Twitter accounts were compromised and the hackers used the accounts to tweet about a bitcoin doubling scam. According to multiple reports, a Twitter employee was paid to give the hackers an internal tool that let them leverage high-profile social media accounts.
It was a crazy day in the world of cryptocurrencies, as a massive number of high-profile people and organizations like Bill Gates, Apple, Uber, Barack Obama, Elon Musk, Jeff Bezos, Joe Biden, and many others had their Twitter accounts hijacked. After the incident, a number of armchair sleuths and investigative journalists uncovered a wealth of information about the Twitter issue.
The popular columnist Joseph Cox detailed that he obtained “leaked screenshots” of an internal tool that was used by the hackers. According to the report, Cox says that one of his anonymous sources revealed that the culprits “paid [a] Twitter insider.” He also mentioned that Twitter was still investigating whether or not the employee leveraged the tool or merely allowed others to use it.
On Twitter, the Block Crypto analyst Larry Cermak’s recent Twitter thread gives a comprehensive look at the incident as well. Cermak says that it “all started at 2:16 PM ET with a known crypto account @Angelobtc asking for payment to join a fake telegram paid group.”
“The takeaway is that the hacker started with large crypto accounts and stuck to only a few formats and addresses,” Cermak continued. “The hacker then moved to non-crypto celebrities two hours after the first hack. They only used three BTC addresses. What I will say is that it’s totally unacceptable that it took Twitter to act as long as it did. At 4:17 PM ET it was absolutely clear to anyone that was paying attention that Twitter is compromised. It took Twitter 2 hours (at 6:05 PM ET) to start acting.”
Another finding stemming from Joseph Cox explains that U.S. Senator Ron Wyden complained to Twitter about using end-to-encryption (e2e) for direct messages two years ago, and the firm never acted upon the idea.
“In September of 2018, shortly before he testified before the Senate Intelligence Committee, I met privately with Twitter’s CEO Jack Dorsey,” Wyden tweeted. “During that conversation, Mr. Dorsey told me the company was working on end-to-end encrypted direct messages.” The Senator continued:
It’s been nearly two years since our meeting, and Twitter DMs are still not encrypted, leaving them vulnerable to employees who abuse their internal access to the company’s systems, and hackers who gain unauthorized access.
You know what the real news is from this incident?
Someone appears to have root level access to Twitter. They OWN this platform. They are in GOD MODE. They can do ANYTHING they want on it.
And their top choice is to trick you into parting with your precious bitcoin.
— Jameson Lopp (@lopp) July 15, 2020
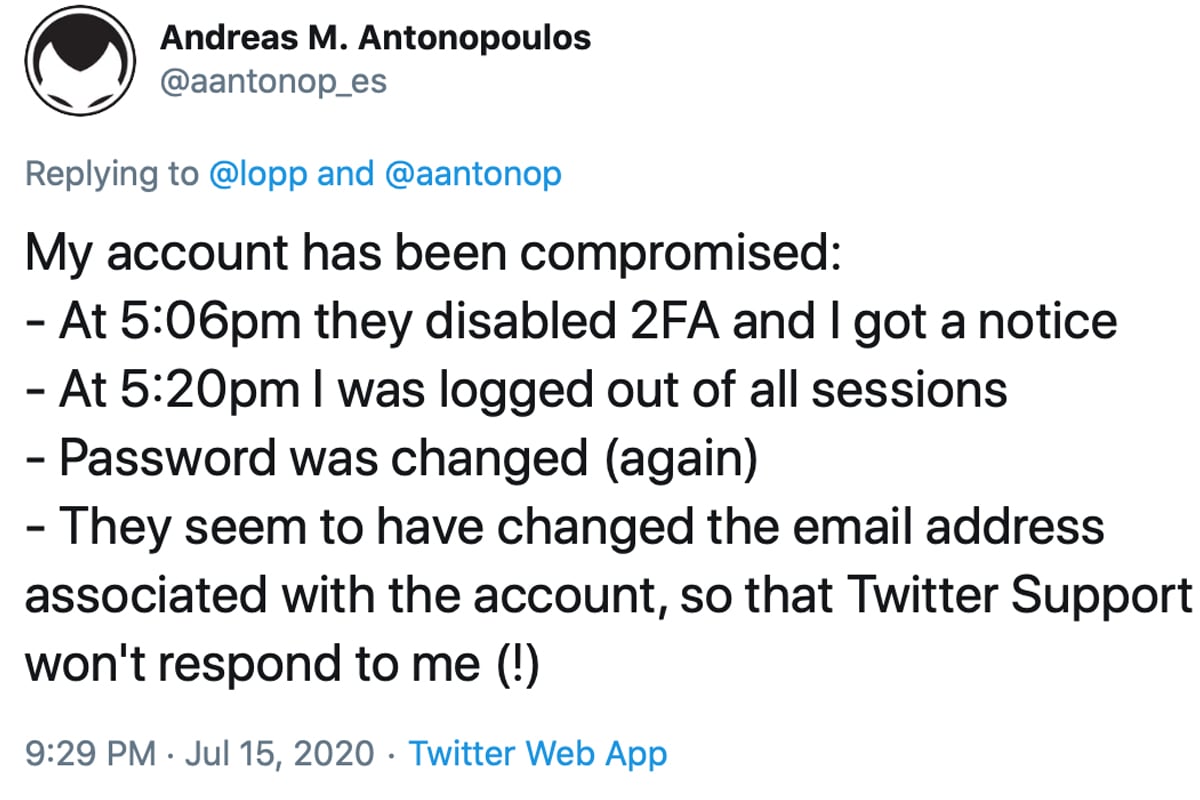
Many people are concerned about the direct message access, as any person who was hacked in the incident may have had their chat logs scraped. The organization Fight for the Future tweeted a petition to the masses in order to convince Twitter CEO Jack Dorsey to protect an account’s direct messages. “It’s long past time for Twitter to implement default end-to-end encryption on direct messages,” the group said. The Electronic Frontier Foundation (EFF) director of cybersecurity, Eva Galperin, also told the public in a tweet that the EFF was also begging Twitter to implement e2e.
“Twitter wouldn’t have to worry about the possibility that the attacker read, exfiltrated, or altered DMs right now if they had implemented e2e for DMs like EFF has been asking them to for years,” Galperin tweeted after the event.
In addition to the famous people and organizations that saw Twitter accounts compromised, the crypto community has been abuzz with the conversation. The blockchain intelligence researchers, Whitestream, believe that some of the bitcoin addresses used during the Twitter incident sent funds to known Bitpay and Coinbase addresses. Twitter also responded to the hacking incident and noted that it was aware of the coordination with an insider. Twitter said:
We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools. We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf. We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.
By the end of the day, armchair sleuths noticed that the hackers raked in more than $114,000 worth of BTC and sent out more than half of the funds to external wallets. Moreover, the accounts that were hacked had an aggregate total of close to 140 million Twitter followers.


Speaking about the subject in an email sent to news.Bitcoin.com Danny Scott, CEO at Coincorner, commented on the Twitter hack fiasco.
“It’s also highly unlikely the hacker did this for monetary gain,” Scott said. “Contrary to what many people still believe, bitcoin isn’t anonymous and all eyes around the world will now be on these bitcoin addresses, and can track where it moves via Bitcoin’s public blockchain.” Scott concluded by adding:
It’s a shame that people are now associating Bitcoin with this Twitter hack as Bitcoin itself has never been hacked and wasn’t the problem in this scenario. The problem was a centralised service (Twitter) which I feel helps emphasize the benefits of Bitcoin’s decentralised nature and how an attack like this could not occur on Bitcoin.
What do you think about the massive Twitter breach and the findings after the incident? Let us know what you think about this subject in the comments section below.
Image Credits: Shutterstock, Pixabay, Wiki Commons, Twitter,
Disclaimer: This article is for informational purposes only. It is not a direct offer or solicitation of an offer to buy or sell, or a recommendation or endorsement of any products, services, or companies. Bitcoin.com does not provide investment, tax, legal, or accounting advice. Neither the company nor the author is responsible, directly or indirectly, for any damage or loss caused or alleged to be caused by or in connection with the use of or reliance on any content, goods or services mentioned in this article.
[ad_2]
Source link



